A while back I blogged about native virtualization on a Mac, and today I am pleased to host Clarence Chio with a guest post about a very interesting use case for using Veertu.
Clarence is a Security Research Engineer at Shape Security, working on the system that tackles malicious bot intrusion from the angle of big data analysis. Clarence has presented independent research on Machine Learning and Security at Information Security conferences in several countries, and is also the organizer of the “Data Mining for Cyber Security” meetup group in the SF Bay Area.
And without further ado…
Malware testing is a common task in a security professional’s workflow. For the uninitiated, malware testing involves examining the behavior and capabilities of malicious software by executing it in a controlled but realistic environment.
Why do malware testing?
On one level, you will be able to observe the malware’s actions close up, and understand how a piece of malware can impact (or has impacted) your systems. On a deeper level, you can dive into the actual code and use disassembly tools to perform binary analysis. Doing this can help you understand exactly what the malware is doing, and in some cases even find ways to neutralize the threat.
Windows malware often latch themselves onto the system by making changes to the Windows registry and/or filesystem. Malware that make network calls often also “phone home” to a Command and Control (C&C) host to exfiltrate information or receive further instruction on what to do after infection. By performing malware testing, all of what the malicious applications do will no longer be a mystery. You have a chance to peek through the fences and understand how attackers think.
How to do malware testing?
Malware testing is typically done in Virtual Machine (VM) lab environments. In this post, I will walk you through a series of steps that you can follow to set up your own Windows 7 malware testing lab on your Mac OS X machine using Veertu. The benefits of using Veertu over other legacy OS X virtualization software mainly comes from Veertu’s implementation of a native hypervisor using Apple’s newly released Hypervisor.framework, resulting in a lightweight yet well-encapsulated solution for virtualization on Macs. In my comparisons, VMs performed significantly better on Veertu compared with alternatives, with a smaller host memory footprint and CPU utilization. This allows you to use system resources more efficiently and ensure that the malware runs on an environment that is as similar to bare-metal as possible.
In addition, Veertu’s “VM read-only” mode allows you to make a base-VM which you can make ephemeral changes to. Any effects and stored system state that the malware has on the read-only VM will be completely and safely removed simply after restarting the VM process. This is analogous to many legacy virtualization software’s “snapshot” functionality, but comes without the hassle of having to manually snapshot system state, manage snapshots, and potentially accidentally retaining some malicious state stored on the machine after reusing the VM.
Getting started with Veertu malware analysis
First of all, you need a paid version of Veertu OS X native virtualization software, as well as a valid Microsoft Windows ISO. You can get Veertu software from your Mac App Store.The free version of Veertu allows you to run a good selection of Linux VMs included in the Veertu Cloud library, but since most malware still target Windows machines, having a Windows malware analysis lab would be nice. After going through the steps of configuring the Windows VM in Veertu, we will have a clean VM that we can start to configure for malware testing.
In this walkthrough, we will be using Windows 7 Home Premium to analyze the Petya Ransomware that has very recently (~ March 2016) become one of the most popular pieces of ransomware in the wild.
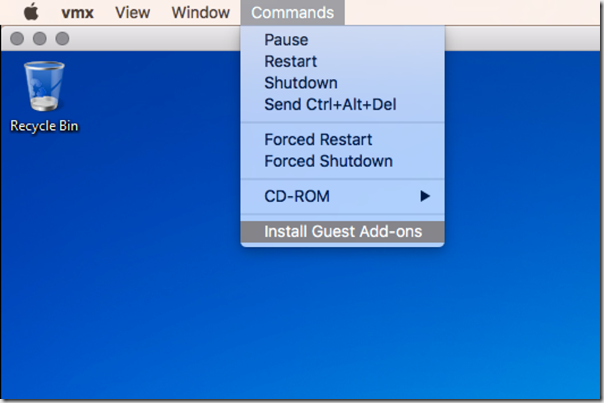
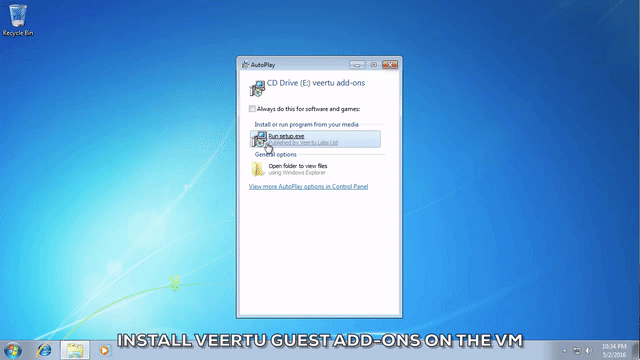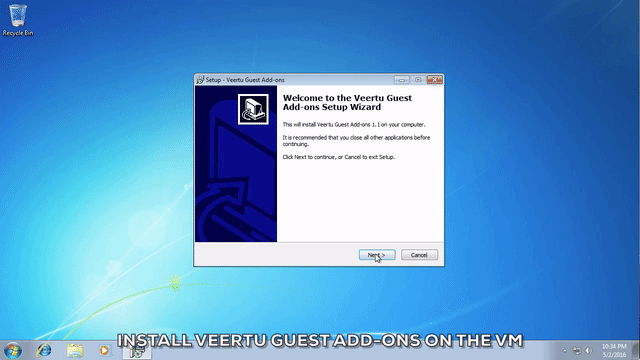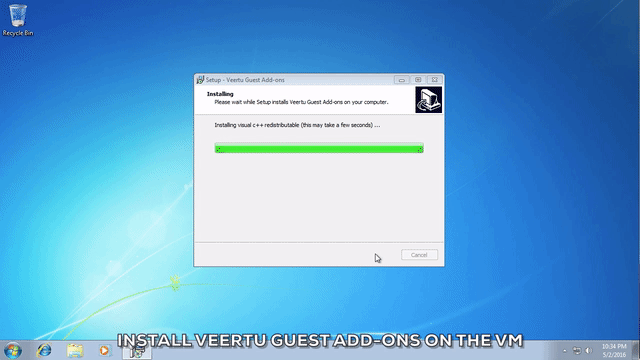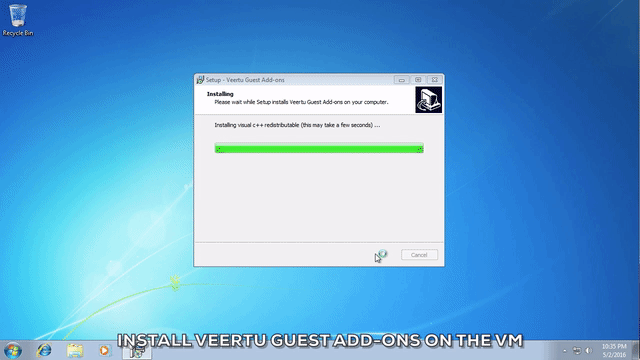
The next thing that you will want to do after launching your Windows VM is to install Veertu Guest Add-ons on your VM. With the Veertu guest VM window selected, click on the “Commands” drop down menu on your Mac menu bar, and select “Install Guest Add-ons”.
This will mount the Veertu Guest Add-ons installation disk as a removable disk in your VM. Simply run the installation script by following through the standard Windows software installation procedure. You will need to restart the OS on the VM for the installation to take effect.
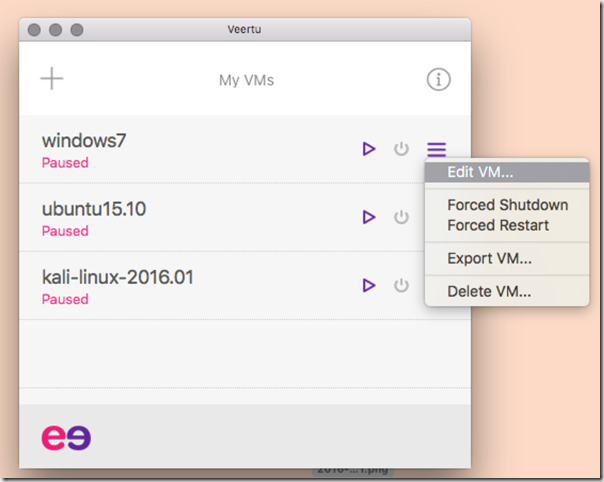
Next, we will set up a shared directory between the Host OS (your Mac) and the Guest OS. (your VM) This allows you to conveniently share files between host and guest systems. In order to do this, open the Veertu VM management window and select the dropdown menu for the VM that we just installed. Click the “Edit VM…” option, and go to the “Advanced” tab. You will be able to configure your shared-folder there.
Malware execution script
For your convenience, here is a simple Windows batch file (.bat) that does 3 simple things:
copy "Z:\malware.bin" "C:\Users\John\Desktop\"
ren "C:\Users\John\Desktop\malware.bin" malware.exe
start /d "C:\Users\John\Desktop\" malware.exe
Copy the malware named “malware.bin” from the shared folder to the Windows Desktop (the Windows user is John in this example)
Rename “malware.bin” to “malware.exe” for conventional Windows execution.
Execute “malware.exe”
For this environment, we want this script to execute automatically upon boot. To do this, simply create a text file named “run-malware.bat” on your Mac and place it in the Veertu shared directory. By default, the shared directory is mounted as a shared network drive, “Z:\\”.
We want this Windows script (called a batch file) to execute automatically on VM boot. To do this, we first move the script from the shared directory to the VM file system.
To make this script run automatically on VM system boot, we go to the Start menu and open the “Startup” folder, then create a shortcut to the script (we copied it to the desktop earlier) and drag the shortcut into the “Startup” folder.
This Windows batch script now runs on system boot.
Enabling Veertu’s Read-Only mode
We are now ready to enable Veertu’s Read-Only mode by going to the same “Advanced” tab in the VM settings window, (as we did when we were configuring the shared folder earlier) and checking the “VM Read-only” checkbox.

After doing this, your VM will be in a read-only state. Any further changes you make to system state will be ephemeral.
Watching the magic happen
Now, you have a malware analysis lab. Let’s demonstrate the efficacy of this lab environment by running malware on it. First, shutdown the VM and prepare your payload.
If you don’t yet have a Windows malware binary at hand, you can find one from reputable online sources such as Malwr.com. Downloading arbitrary binaries from the Internet is as dangerous as it sounds. “Fake” malware analysis sites have been known to exist for the sole purpose of distributing malware. Make sure that your source is reputable. Be extra careful in doing this, and make sure that you do not execute any of the binaries that you download on your host operating system. Most malware binaries that you download from these sites come with the “.bin” extension, as an entry-level measure to prevent you from executing it by accidentally clicking it.
Rename the malware to “malware.bin”, and place it in the Veertu VM shared directory. Then, start the VM. The script should start once the system boots.
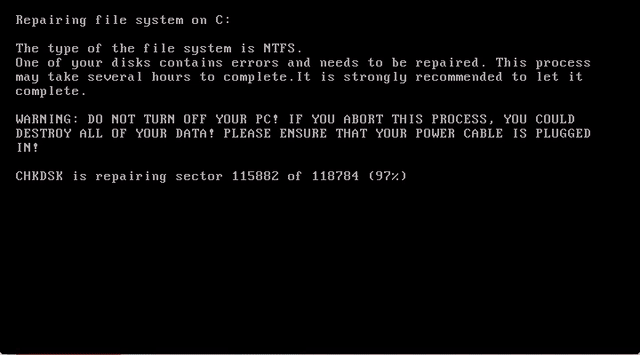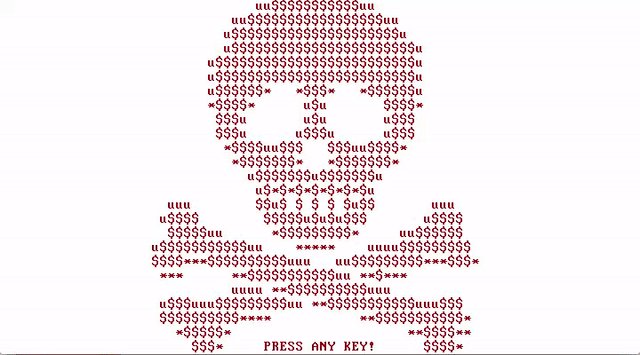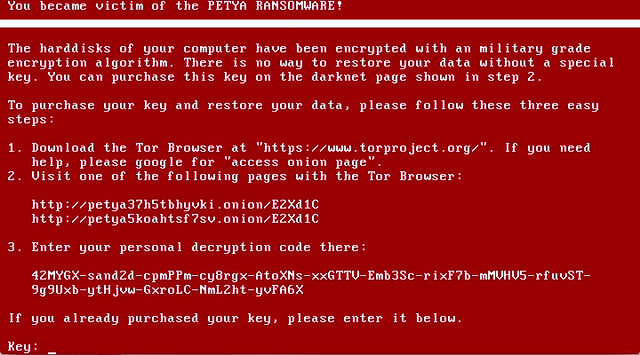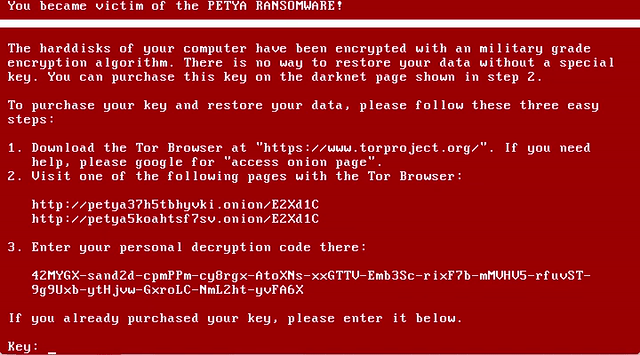
It works! The Petya Ransomware executes, and the system immediately reboots to a fake DOS screen stating that it is “Repairing file system on C:”. What the malware is actually doing is encrypting your “C:”. Once the encryption is done, it promptly informs you that you have fallen victim to the Petya Ransomware, and you need to pay some Bitcoin for the decryption code. We chose this particular ransomware for the demonstration because it is particularly tricky to get rid of. Even though it is possible to decrypt your hard drive without paying the ransom, it requires the physical removal of your hard drive.
Here comes the magic. Simply power-off the VM, remove the malware binary from the shared directory, and restart the VM. No more trace of the malware, and the VM’s hard disk image is no longer encrypted. As you might imagine, this shaves many cycles off the malware testing workflow, and gets rid of any VM snapshot management intricacies. You have a malware testing environment that you can use over and over again without having to reprovision or reinstall any tools on the guest OS.
Performing further analysis
Of course, just observing malware execution behavior by running the executable can hardly be called malware “analysis”. Browse the huge open-source list of Awesome Malware Analysis tools and more in-depth tutorials for how you can get started with observing malware behavior and perform binary analysis to dive into actual malware code.
Once you have identified set of malware analysis tools that you can use to perform deeper malware introspection, simply turn off Veertu’s VM read-only mode to install these tools, then turn read-only mode back on, and continue analyzing malware.
Fin
“To know your Enemy, you must become your Enemy.”
- Sun Tzu’s “The Art of War”
Malware testing allows you to gain a deep understanding of the threats to your system, and understand trends in malicious software. And, if your are a Mac user, then, with Veertu, you can create a highly optimized and streamlined malware analysis lab environment that you can use to dissect malware behavior.